Ransomware – to pay or not to pay?

As CEO of a cybersecurity company, I get asked all the time about ransomware. It’s become the new party question – do you pay or not pay the ransom?
On one hand, I appreciate the attention that is finally being paid to cybersecurity, because for those of us working in the industry, we have been demanding more attention for many years. We want people to take cybersecurity seriously, and to understand the positive impact it can have on individuals and businesses.
On the other hand, however, while ransomware is topical and an interesting conversation starter, I find that leaders leave without any strategy or plan for what to do, other than be afraid.
One Friday afternoon this summer as I was developing a presentation about ransomware for an event, I got a call from a colleague who asked if we were able to help a friend who thought their organization was hit with ransomware. What are the chances? Well, really good, because not only are we seeing a huge rise in cyber crime, but it also almost always happens on Friday afternoon!
With discretion in mind, we started with a phone call between me and the leadership team. From there our incident response team jumped into gear and helped navigate the organization through the process. For several weeks, we worked with their team to recover from the incident, and as I went through the meetings and conversations with the leadership team and board of directors, I couldn’t help but to be intrigued by the emotional journey they were all going through.
While we must understand the technical recovery journey of a ransomware attack, we must also understand the emotional journey we take in tandem – “The Ransomware Rollercoaster”.
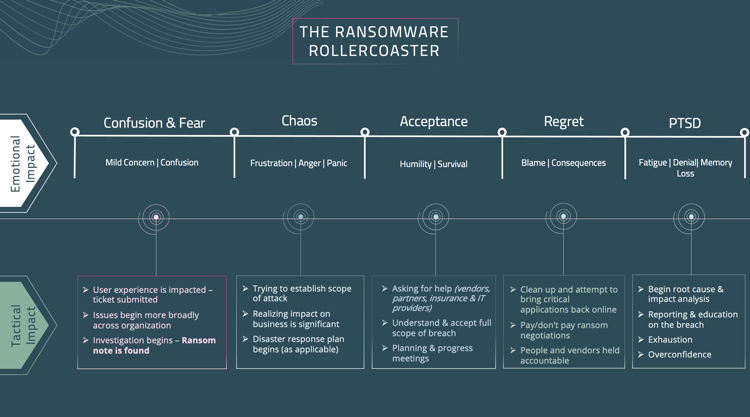
Like many other ransomware events, this one started out with confusion and fear, as one HelpDesk ticket quickly turned into multiple HelpDesk tickets. Systems were up and reachable but not working quite right. After some troubleshooting, one of the techs finally discovered a note from the hackers in the logs of the server. It was too late – the team was locked out.
Thus began the chaos stage.
The leadership team and IT team panicked. All the “what-ifs” and “why us” conversations began to unfold. People created scenarios and made assumptions as the significance of the event rapidly sank in. People were angry, frustrated and pointing fingers at vendors. The entire staff was scared because they realized they weren’t prepared and needed to figure out a plan fast.
Enter the Acceptance Phase.
During that time, survival mode kicked in. The team was trying to build a response team of lawyers, PR strategists, IT experts and more that would help address the full scope of the problem. Of course, Friday night, with no IT systems, makes that a tough situation. Emotions continued to flare.
Finally, by Sunday the tone changed, partly because people were sleep deprived (which is a hugely underrated impact of cyber events), but also because people began to accept the reality of the situation. Like any traumatic event, people deny the reality for a while, as they process their emotions. As reality set in, team members went from angry and indignant to humble. People began to realize that mistakes were made, and as the full scope of the breach became clearer, it was understood that tough decisions had to be put into action.
Regrets
Once a plan was in place and the environment stabilized, the recovery phase continued, it often does for many months. Decisions were made during this time such as whether to pay or not pay the ransom, how and when to bring critical applications back online and, unfortunately, determine who is to blame … the feeling of regret is strong, which leads to terminations, new vendors and policy changes.
The Aftermath
Slowly the team recovered, losing time and money and productivity along the way.
Due to the stress, and fear, these quick decisions made during a ransomware attack are extremely reactive. Adrenaline drives quick action but that rarely results in the most efficient or effective outcomes.
Once those decisions are made, the fatigue sets in, and people disconnect. Oftentimes there is a feeling of denial or overconfidence that it could ever happen again. But rest assured, it absolutely can.
Living through a ransomware event isn’t fun. Living through it unprepared is even worse.
What can be done differently?
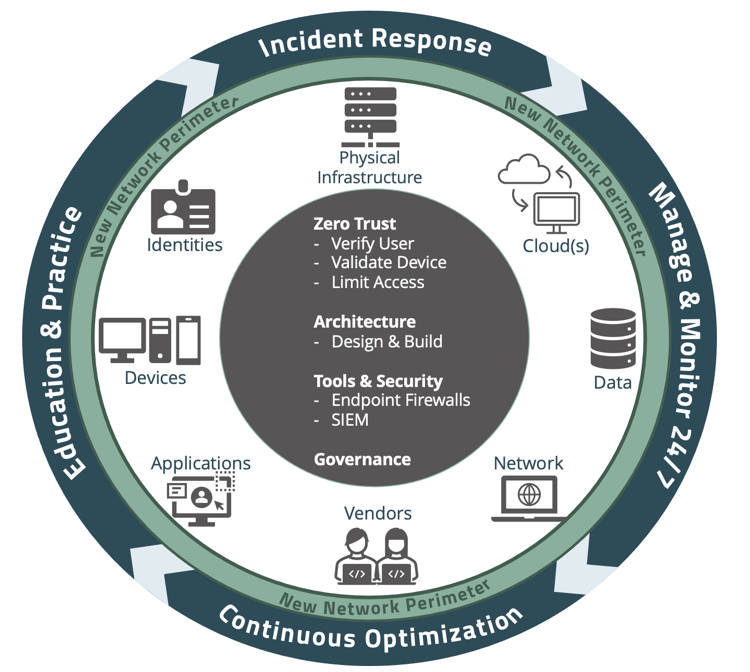
Leadership teams must be able to understand, manage and reduce their risk, while prioritizing investments in cybersecurity. Organizational leadership should also be able to efficiently and effectively communicate their current and/or desired cybersecurity posture internally and externally. Leadership teams can do this by utilizing resources like the Cybersecurity Framework 101 and referencing cybersecurity checklists.
Build a team of qualified partners, and practice as you would with a fire drill. Cyber attacks can be complex, and require multiple teams and resources taking the right steps at the right time. In the case of an actual event, the team will be prepared to respond rather than frantically trying to figure out what to do and losing precious time.
Protecting an organization from ransomware attacks requires continuous attention as hackers get more creative, aggressive and brazen. All employees should be trained to understand the threats and how they can proactively protect themselves and the company.